Anatomy of a Hack: How Design Decisions Led to the USPD Exploit
The CPIMP attack on USPD exposed some weaknesses in our early architectural choices. Based on our current analysis, these choices contributed to the conditions that made the exploit possible, and this post explains how.
This post expands on our Preliminary Postmortem which covers the technical details of the CPIMP attack itself, and our Path Forward which outlines our recovery plan and V2 roadmap.
- Root cause: A window between proxy deployment and initialization allowed a CPIMP shim to be installed. No keys or multisigs were compromised.
- Impact: The attacker gained upgrade-equivalent control of the StabilizerNFT proxy and later drained via that control path.
- Visibility: Our legitimate initialization still succeeded because the shim reset its own initialized flag. Block explorers showed benign implementation addresses.
- Actions taken: Paused minting, engaged law enforcement and SEAL 911, notified CEXs/DEXs, began funds tracing.
The Decision: Deterministic Addresses Across All Chains
Early in 2025, when we started building USPD, we decided to deploy all contracts to the same address on every EVM chain using CREATE2.
The benefits seemed clear:
- Simplified UX: Users interact with the same addresses regardless of chain.
- Easier integrations: Partners only need to whitelist one set of addresses.
- Cross-chain consistency: Documentation and tooling work universally.
- Scam prevention: One canonical address helps users spot fakes on other chains.
This decision alone is not problematic. Many protocols use CREATE2. The complexity came from how our contracts interact with each other.
The Problem: Circular Dependencies
Our architecture has multiple contracts that need to know about each other during deployment. Looking at our deployment script (04-DeploySystemCore.s.sol), the dependency graph is messy:
┌─────────────────┐ ┌─────────────────┐ ┌─────────────────┐
│ StabilizerNFT │────▶│ cUSPDToken │────▶│ USPDToken │
└─────────────────┘ └─────────────────┘ └─────────────────┘
│ │ │
│ ▼ │
│ ┌─────────────────┐ │
│ │ RateContract │◀────────────┘
│ └─────────────────┘
│ ▲
▼ │
┌─────────────────┐ │
│ Reporter │─────────────┘
└─────────────────┘
▲
│
┌─────────────────┐
│ StabilizerNFT │ (circular!)
└─────────────────┘Here is what each contract needs at initialization:
| Contract | Dependencies Required |
|---|---|
| cUSPDToken | Oracle, StabilizerNFT (proxy address), RateContract |
| USPDToken | cUSPDToken, RateContract |
| Reporter | StabilizerNFT (proxy address), RateContract, cUSPDToken |
| StabilizerNFT | cUSPDToken, stETH, Lido, RateContract, Reporter, InsuranceEscrow, EscrowImplementations |
StabilizerNFT needs Reporter. Reporter needs StabilizerNFT.
Also, cUSPDToken needs the StabilizerNFT address, but StabilizerNFT needs cUSPDToken to be deployed first so it can be passed during initialization.
Why Not Just Use Setter Functions?
Why not deploy contracts with placeholder addresses and update them via setter functions afterward?
We considered this, but we had reasons to use immutable arguments:
-
Contract Size Limits: Our StabilizerNFT was close to the 24KB limit. Every setter function adds bytecode. We could not afford multiple setters.
-
Immutability as Security: We wanted contracts to be immutable. When you look at a deployment, you should see exactly what it is configured to do. No hidden admin functions to change critical addresses later.
-
Minimizing Upgrade Surface: We wanted to deploy, verify, and revoke upgrade capabilities. Setter functions require keeping admin keys active longer.
-
Audit Scope: Every setter function is an attack surface. Auditors need to verify access controls and reentrancy for functionality we would only use once.
The “Solution”: Deploy Proxy First, Initialize Later
To fix the circular dependency while keeping addresses deterministic, we used a specific pattern:
- Deploy the StabilizerNFT implementation (no dependencies needed).
- Deploy the StabilizerNFT proxy pointing to the implementation, but do not initialize it yet.
- Deploy cUSPDToken (can now reference the proxy address).
- Deploy USPDToken (references cUSPDToken).
- Deploy Reporter (references the proxy address and cUSPDToken).
- Deploy InsuranceEscrow (references the proxy address).
- Now initialize the StabilizerNFT proxy with all the addresses.
This is in our deployment script:
function run() public {
vm.startBroadcast();
deployStabilizerNFTImplementation();
deployStabilizerNFTProxy_NoInit(); // <- THE FATAL STEP
deployCUSPDToken();
deployUspdToken();
deployReporterImplementation();
deployReporterProxy();
deployInsuranceEscrow();
initializeStabilizerNFTProxy(); // <- Initialization happens later
setupSystemRoles();
saveDeploymentInfo();
vm.stopBroadcast();
}The gap between deployStabilizerNFTProxy_NoInit() and initializeStabilizerNFTProxy() is where the attacker struck.
We did not know about the CPIMP vulnerability. We thought if someone front-ran our initialization, we would see it. The transaction would fail or behave unexpectedly, and we would redeploy. It did not look like that happened when we deployed. Everything appeared normal. We continued operating on the proxy with the shim installed.
The Attack: A Sandwich
This was not a simple shim installation with a generic initialize() call.
Block-by-Block Timeline
| Block | Transaction | Description |
|---|---|---|
| 23375794 | 0x3477bb… | Our proxy deployment (uninitialized) |
| 23375795 | 0xc0b7e4… | Attacker’s Multicall3 sandwich |
| 23375797 | 0xe03809… | Our initialization (succeeds, but proxy already compromised) |
The attacker inserted their transaction one block after our proxy deployment and two blocks before our initialization.
Not a Generic Attack
Our initialize function takes 10 parameters:
function initialize(
address _cuspdToken,
address _stETH,
address _lido,
address _rateContract,
address _reporterAddress,
address _insuranceEscrowAddress,
string memory _baseURI,
address _stabilizerEscrowImpl,
address _positionEscrowImpl,
address _admin
)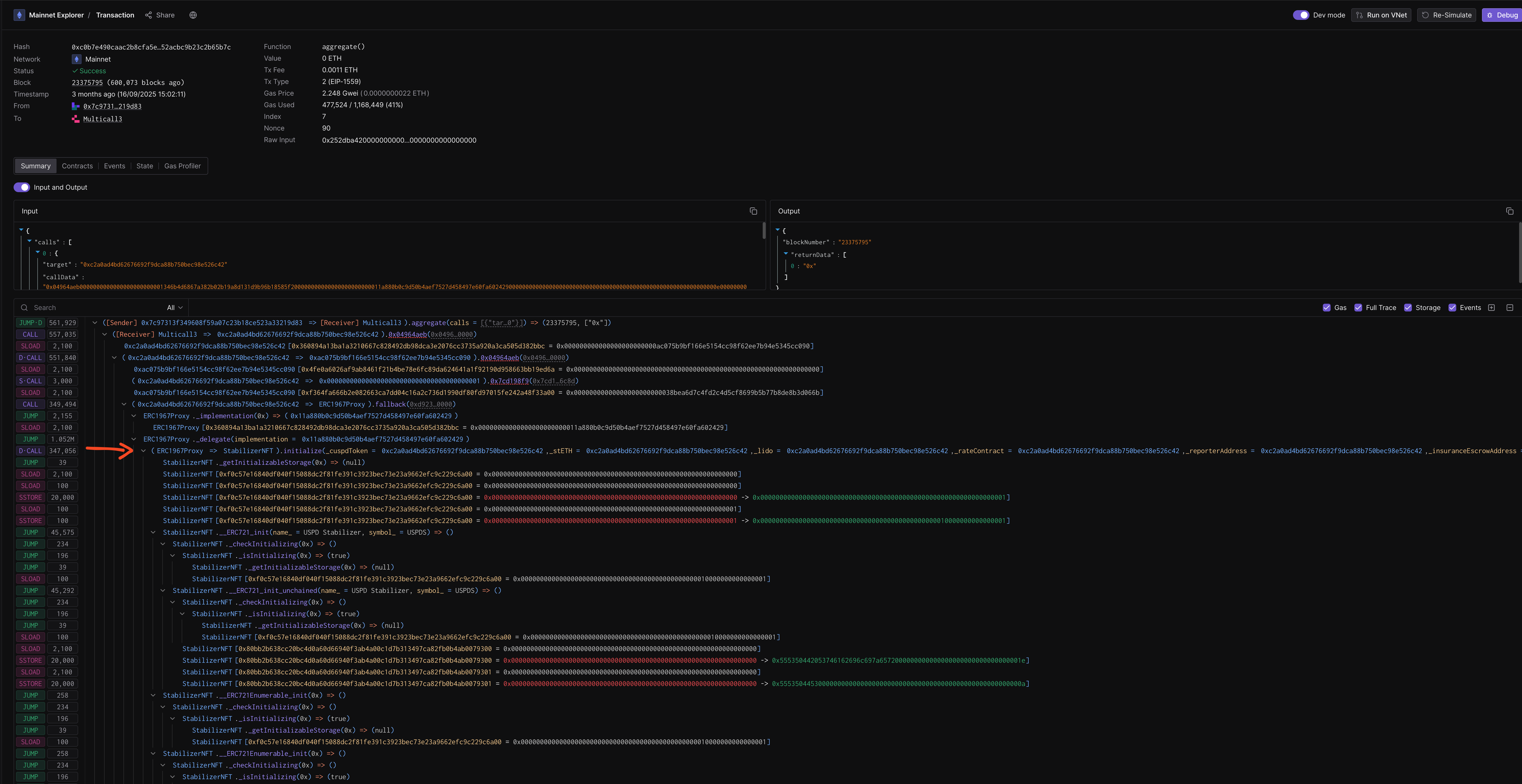
The selector is 0xd9230389. It is not the standard initialize() or initialize(address).
The attacker could not simply listen for generic initialize calls. They had to:
- Detect our proxy deployment.
- Analyze the implementation contract to find the initialization function.
- Determine the correct function signature and parameter types.
- Craft valid parameters.
- Package everything into a Multicall3 transaction.
- Submit it before our initialization landed.
They had about 11 seconds to do this.
Using Our Own Implementation Against Us
The attacker called our legitimate implementation’s initialize function with substituted parameters. The execution flowed through our own contract code.
At the end, the attacker:
- Set their own storage variables for the CPIMP shim.
- Reset the
_initializedflag back to 0.
This last step is crucial. When our actual initialization transaction landed two blocks later, it succeeded without reverting. The proxy appeared to initialize normally. We had no indication anything was wrong.
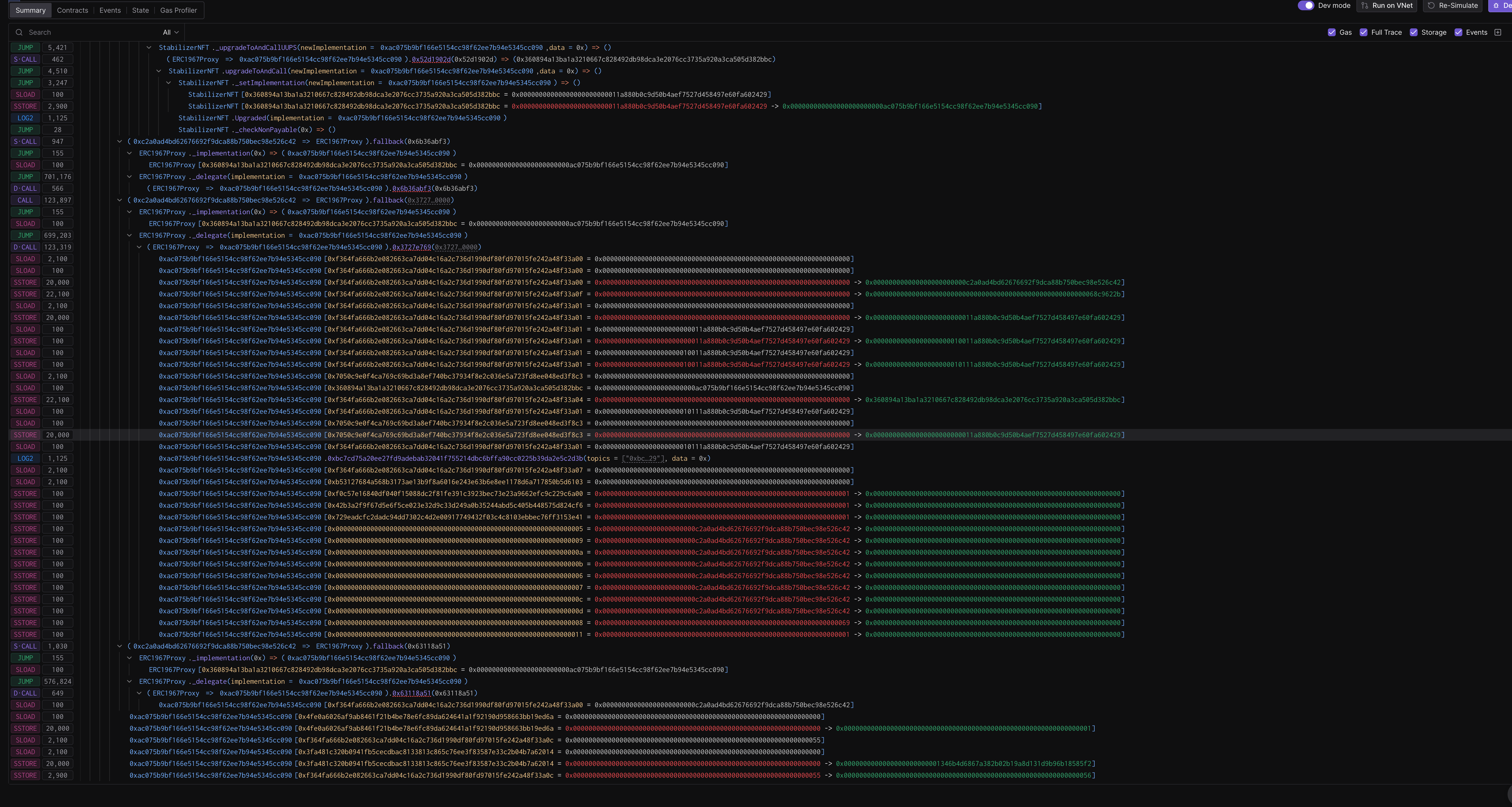
The Shim: A Masterpiece of Stealth
We analyzed the attacker’s shim (0xAC075b9bf166e5154Cc98F62EE7b94E5345Cc090). It aligns with findings by pcaversaccio and Dedaub. It is designed to look like a legitimate upgradeable proxy while secretly maintaining a “Shadow Administration” layer.
The “Shadow Admin” Mechanism
The shim hardcodes a secret administrator address that bypasses all onlyOwner checks:
// In multiple functions (e.g., 0x9441e515, 0x8c84497d)
address owner = stor_f364...00; // Reads from hidden slot
if (msg.sender == owner) {
// BYPASS: Grants full access
} else {
// Fake check to make it look legitimate or delegate to real impl
}The “Trojan Horse” Storage Layout
The shim maintains two parallel implementation pointers:
- Public Implementation (
0x3608...): Derived frombytes32(uint256(keccak256('eip1967.proxy.implementation')) - 1). Points to the Shim itself (or a fake benign contract) so block explorers show “Verified Source.” - Shadow Implementation (
0x7050...): Derived fromkeccak256("org.zeppelinos.proxy.implementation"). Points to the Real Malicious Logic (or your original logic when they want to hide).
The shim decides which one to use based on the function selector:
// In function 0x30e3 (Fallback/Delegate logic)
if (selector == 0x4f1ef286) { // upgradeToAndCall
// Hijack the upgrade process
} else {
// Delegate to the shadow implementation
delegatecall(stor_7050...);
}When you call the contract, it works. When they call it, they hit their backdoors.
Why Counter-Attacks Are Nearly Impossible
We looked at surgically removing this shim without abandoning the proxy address. It is risky because the shim intercepts upgradeToAndCall.
The Problem: Interception
If you call upgradeToAndCall(newImpl, data), the Shim’s logic at 0x4f1ef286 executes:
- It checks
msg.sender == admin(which might be you, OR it might be overridden to be the attacker). - Even if it allows the upgrade, the Shim often only updates the “Public” implementation slot while keeping the “Shadow” implementation active.
- It might block upgrades unless they come from the attacker.
The “Storage Nuke” Strategy
To reclaim the proxy, you must bypass the Shim’s logic entirely or trick it into overwriting its own brain. Since you cannot bypass the code execution, you must find a path that allows arbitrary storage writes.
Why Automated Detection Is Hard
These shim contracts are hard to find automatically. You cannot reliably search for specific storage slot patterns because the attacker can change them.
The storage slots we identified (STOR_FF36_OPERATOR, STOR_10F3_LEGIT_IMPL) are just the ones this attacker used. Tomorrow, they could deploy a new shim with different slots and logic. Any automated detection tool built today will be obsolete when the attacker adapts.
There is no silver bullet for detecting CPIMP infections after the fact. The only reliable defense is prevention: atomic deployments, verified initialization, and owning every step of your deployment process.
The Scale Question: Targeted or Automated?
We scanned for state diffs from mainnet from block 21047124 and marked infected contracts.
Key findings:
- First CPIMP infection: Block 21864585 on 2025-02-17 07:22:59 UTC from
0x00bda7096754410b9caa2b559fb263cda1b1b243. - Last infection: Infections are still occurring.
- Total infections found: ~200 proxies.
- Infections after our deployment: ~30.
We also searched for proxies deployed uninitialized that were later initialized. Even same-block transactions got bundled together. From the 208 infected proxies we found, this occurred in 94 cases - about 50% of them.
Atomicity in contract creation + initialization is necessary. Even same-block deployment and initialization is not safe. The attacker can bundle their transaction in the same block. True atomicity requires a single transaction.
The sophistication required suggests this is not a casual operation. This is infrastructure built for scale, likely part of a larger MEV/searcher operation. Our sandwich attack specifically came via BuilderNet as far as we can tell.
However, several forensic clues point towards a semi-professional, more small-scale group with access to scanning infrastructure rather than a real nation-state actor:
- Storage Slot Reuse: The attacker uses the same storage slots across multiple shims. A more sophisticated actor might randomize these to evade detection for longer.
- Address Reuse: We observed potential reuse of addresses across different operations, including the same shim used dozens of times.
- Operational Errors: When moving funds to Tornado Cash, one transaction was slightly underpaid and remained pending for a while.
- “Petty Cash” Behavior: The attacker is currently draining small amounts from the Curve pools. This “scraping the barrel” behavior is inconsistent with typical nation-state targets.
We do not have data on how many other protocols have been compromised. The CPIMP attack is designed to be invisible until exploitation. This attack targets the trust developers place in their deployment scripts. It exploits the assumption that a deployment can be verified by looking at the transactions and general state.
We were one of ~200 victims. We will not be the last.
Why We Didn’t Catch It
The Attack Vector Was Unknown To Us
When we wrote this deployment script in early 2025, we did not know about CPIMP. The attack was first publicly disclosed by pcaversaccio on X/Twitter in July 2025 - months after our architecture was finalized.
Our final security audits were completed on August 20, 2025. Neither we nor our auditors (Nethermind and Resonance) were aware of this vulnerability. The disclosure in July mitigated a large-scale attack before it caused damage, so there was no media outcry. It never reached us.
We deployed on September 16, 2025. The attacker sandwiched our initialization.
We Were Busy Building
Between audit completion and deployment, we were:
- Finalizing contract changes.
- Building the frontend.
- Marketing.
- Preparing documentation.
The CPIMP attack generated little noise in the security community because the mitigation was successful. We were not monitoring security Twitter 24/7. We were building.
Some say we should have had dedicated security personnel. But this vector was not widely known, even among professionals. It is a supply-chain attack that bypasses traditional audit scopes.
Everything Looked Right
After deployment, we checked:
- ✅ All transactions succeeded.
- ✅ Etherscan showed our legitimate implementation.
- ✅ All contract functions worked.
- ✅ Our initialization transaction completed successfully.
- ✅ Nobody seemed to have front-run us.
The CPIMP attack is designed to be invisible. The attacker’s contract forwards all calls to the legitimate implementation. There were no visible signs of compromise.
Addressing the “Inside Job” Narrative
We have seen speculation that this was an inside job. The timing seems perfect and the attack sophisticated.
Here is what we know:
- The attacker’s infrastructure has infected ~200 proxies across the ecosystem.
- The attack pattern is consistent across all victims.
- The attacker waited nearly three months before draining funds. This suggests automated monitoring rather than insider knowledge.
- Our upgrade attempt on December 4th likely triggered their monitoring systems. They drained within minutes.
This was not someone with insider access. This was industrial-scale infrastructure designed to exploit uninitialized proxies. We ended up using this pattern because it solved our specific architectural constraints at the time. So did ~199 other contracts.
The attacker is not targeting USPD specifically. They are targeting every team that deploys an uninitialized proxy.
The Trigger: A Routine Upgrade
For nearly three months, the infected contracts operated normally. Users minted USPD, stabilizers deposited collateral, yield accrued.
On December 4th, 2025, we attempted a routine upgrade to fix a minor bug in the StabilizerNFT. This likely triggered the attacker’s monitoring systems.
The execution of the attack happened in three steps:
- Deployment of Intermediary: The attacker deployed a contract at
0x77b2a9261D53e4F001b6F821f6beA003a31b3484(Tx:0x02f3cf5bc9bfdf02e38febe947e323d8eb2a275920e1980719a966ac8923c799). - Deployment of Malicious Logic: They deployed a modified version of our StabilizerNFT at
0xa3D2616Ee942b36648eaA55976eE7B761bd2a21B(Tx:0x6a748155bb97e5d25626173593060ee2f6bc76174541e5b1ef9690f8d895e9f2). This contract seems to have been hastily crafted: decompilation shows it still contains our original overcollateralization checks, just modified to allow the withdrawal. - The Drain: In transaction
0xa7cab072bf0453301a0ab1b06c49a9405d115824fc617fb42cba9b70f3b893c2, they calledupgradeAndCall. This updated the implementation to0x77b..., which then calledupgradeAndCallon the StabilizerNFT to switch to the malicious0xa3D...logic. This logic executed the drain to0x083379bdac3e138cb0c7210e0282fbc466a3215a.
Initially, we thought we introduced a bug during the upgrade. It was only through forensic analysis that we discovered the attacker had been “super admin” since the first block of the proxy’s existence.
What Other Teams Can Learn
We are sharing this because we do not want other teams to make the same mistakes.
1. Never Deploy Uninitialized Proxies
If you must use the deploy-then-initialize pattern, do it in a single atomic transaction. Use a deployer contract that:
- Deploys the proxy.
- Immediately initializes it.
- All in one transaction that either fully succeeds or fully reverts.
// BAD: Two separate transactions
proxy = deployProxy(implementation);
// ... attacker can front-run here ...
proxy.initialize(params);
// GOOD: Single atomic transaction
proxy = deployAndInitialize(implementation, initParams);Even same-block is not safe! Our research found that ~50% of infected proxies had their legitimate initialization in the same block as the CPIMP attack. The attacker can bundle their transaction alongside yours. True atomicity requires a single transaction.
2. Own Your Stack Trace
Do not just check that your transaction succeeded. Understand everything that happened. After any deployment:
- Trace the full execution path.
- Verify every storage slot that was written.
- Check that no unexpected contracts were called.
This is tedious. It is also the only way to catch sophisticated attacks. Block explorers and “transaction succeeded” messages tell you nothing about what actually happened under the hood.
3. Never Rely Solely on Audits
We paid for two professional audits. We are grateful for the work Nethermind and Resonance did. But audits are not enough.
4. Stick to Proven Patterns
Our desire for deterministic addresses and immutable configurations added complexity. That complexity created a vulnerability. Deterministic addresses do not help if initialization can be hijacked. Prioritize safe, atomic initialization over address determinism.
5. Stay Connected to Security Research
The CPIMP attack was disclosed ~2 months before we deployed. If we had been plugged into security research channels even more, we might have caught it.
What We Are Doing Differently for V2
USPD V2 will feature:
-
Atomic Deployment: All proxy deployments will include initialization in a single transaction. No gaps.
-
Simplified Dependency Graph: We are redesigning the architecture to minimize circular dependencies. Fewer dependencies means simpler deployment.
-
Modular Contracts: Instead of one large StabilizerNFT, we are breaking functionality into smaller contracts.
-
Manual Verification: We will manually trace and verify every storage slot and execution path after deployment. No automated tools. Human eyes on every transaction.
For details on V2, see our Path Forward post.
Acknowledgments
Thank you to:
pcaversaccio for the original public disclosure of the CPIMP attack in July 2025. This research was critical.
SEAL 911 (X/Twitter ) for their immediate response. They helped by:
- Flagging our token at CEXs and DEXs.
- Coordinating with block explorers.
- Pointing us in the right direction.
If you ever experience a security incident, SEAL 911 is an invaluable resource.
A Note on Block Explorer Warnings
In the original Dedaub article about the CPIMP attack, they mentioned that Etherscan would mark these contracts.
This has not happened yet. The last CPIMP infection we detected was from today, and infected contracts still show misleading implementation information on block explorers. Do not rely on block explorer warnings. Verify storage slots directly.
Closing Thoughts
Every decision we made seemed reasonable at the time.
- Deterministic addresses? Industry best practice.
- Immutable configurations? More secure than setter functions.
- Minimal upgrade surface? Reduces long-term risk.
But combined with an unknown attack vector, these decisions created a vulnerability we could not see.
The hardest part of security is protecting against attacks that do not exist yet. We failed at that. We own it. We are building V2 with that humility.
To the critics: We followed industry standards. We had two professional audits. We tested. We operated with rigor.
To other teams: Learn from our experience. Atomic deployments. Own your stack traces. Never trust - always verify. Do not let this happen to you.
We are not giving up. We are rebuilding.
Further Reading
- Preliminary Postmortem: The CPIMP Attack - Technical details of the attack
- The Path Forward: USPD V2 - Our recovery plan and V2 roadmap
- pcaversaccio’s original CPIMP disclosure - The tweet that first publicly revealed this attack vector
- Dedaub: The CPIMP Attack - Original security research
- SEAL 911 - Emergency security response for the ecosystem
If you have questions or want to discuss this further, join us on Discord or reach out on Telegram .
- The USPD Team
For clarity, this is the data we put together by looking at state diffs from mainnet:
| id | proxy_address | block_number | timestamp | transaction_hash | transaction_from | implementation_slot_before | implementation_slot_after | admin_slot_before | admin_slot_after | suspicious_slot_changes | suspicion_score | suspicion_reasons | has_double_delegatecall | middleman_address | final_implementation | delegatecall_depth | upgraded_event_count | has_initialized_event |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0x093f7d02ce50048bf71d90fc2e278d84815f977fed740026389b7f3ae00e51af-0xbc2bc8f73d188524d3e96491093800a9517dcc13 | 0xbc2bc8f73d188524d3e96491093800a9517dcc13 | 23974195 | 2025-12-09 09:01:59+00 | 0x093f7d02ce50048bf71d90fc2e278d84815f977fed740026389b7f3ae00e51af | 0xafaa0819f1898585b7547b3fbb89dac72d09946d | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x00000000000000000000000004202d7ec47587562e622a2f4f1fbc7fac588473 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x00000000000000000000000004202d7ec47587562e622a2f4f1fbc7fac588473 | f | 0 | 0 | f | ||||
| 0x44ca11d767bf6208327960111e17d4cd589e8d97635c880a6759b8f378e7fb14-0x250ca2e1a526d23f1df52c2a95b39feb18b13474 | 0x250ca2e1a526d23f1df52c2a95b39feb18b13474 | 23959610 | 2025-12-07 07:57:11+00 | 0x44ca11d767bf6208327960111e17d4cd589e8d97635c880a6759b8f378e7fb14 | 0xafaa0819f1898585b7547b3fbb89dac72d09946d | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x00000000000000000000000004202d7ec47587562e622a2f4f1fbc7fac588473 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x00000000000000000000000004202d7ec47587562e622a2f4f1fbc7fac588473 | f | 0 | 0 | t | ||||
| 0x6f2ef228c234822e5edeb0bcd2a70e4f2d025414c62ea0386d620c45868c12d3-0x04202d7ec47587562e622a2f4f1fbc7fac588473 | 0x04202d7ec47587562e622a2f4f1fbc7fac588473 | 23952318 | 2025-12-06 07:20:47+00 | 0x6f2ef228c234822e5edeb0bcd2a70e4f2d025414c62ea0386d620c45868c12d3 | 0xdf11c64096bd36973eed083f36913fe521cab38e | 0x000000000000000000000000df11c64096bd36973eed083f36913fe521cab38e | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x000000000000000000000000df11c64096bd36973eed083f36913fe521cab38e | f | 0 | 0 | f | |||||
| 0xf27412938362f68fe7b8517a40bea8b037c8bfd517660f085eaa5668f0e970ab-0x377cdba22efe718cc396dd68d999a7033a153b6b | 0x377cdba22efe718cc396dd68d999a7033a153b6b | 23952294 | 2025-12-06 07:15:59+00 | 0xf27412938362f68fe7b8517a40bea8b037c8bfd517660f085eaa5668f0e970ab | 0xe225ba8ac6151968371e518c78d7e1864c49ea64 | 0x0000000000000000000000000000000000000000000000000000000000000001 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x0000000000000000000000000000000000000000000000000000000000000001 | f | 0 | 0 | f | |||||
| 0x0d6f04e819abc4af84c8bfb5b7a1b34a736cca0a11d1aab20e43a8d9551a1e89-0x03a017ea70b17b9c59cfa0ec4b8b010434eca88e | 0x03a017ea70b17b9c59cfa0ec4b8b010434eca88e | 23940949 | 2025-12-04 16:46:23+00 | 0x0d6f04e819abc4af84c8bfb5b7a1b34a736cca0a11d1aab20e43a8d9551a1e89 | 0x5d690febcec4e49d5b4993eb262a51cc4143787f | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x00000000000000000000000073202eb95bac7270b4c494564f862d94d838433a | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x00000000000000000000000073202eb95bac7270b4c494564f862d94d838433a | f | 0 | 0 | t | ||||
| 0xf4e2b1c4d49cfea6281e8a6743f106291cf4b675a48f30f3e488c8d11a821f12-0x77ee252fc6fc18ba1321f221a05fdf8b6eaf50d6 | 0x77ee252fc6fc18ba1321f221a05fdf8b6eaf50d6 | 23931880 | 2025-12-03 08:59:11+00 | 0xf4e2b1c4d49cfea6281e8a6743f106291cf4b675a48f30f3e488c8d11a821f12 | 0x5d690febcec4e49d5b4993eb262a51cc4143787f | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x00000000000000000000000073202eb95bac7270b4c494564f862d94d838433a | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x00000000000000000000000073202eb95bac7270b4c494564f862d94d838433a | f | 0 | 0 | f | ||||
| … | … | … | … | … | … | … | … | … | … | … | … | … | … | … | … | … | … | … |
| 0xc0b7e490caac2b8cfa5e62d1b28a5e7dba7600e623c71352acbc9b23c2b65b7c-0x1346b4d6867a382b02b19a8d131d9b96b18585f2 | 0x1346b4d6867a382b02b19a8d131d9b96b18585f2 | 23375795 | 2025-09-16 13:02:11+00 | 0xc0b7e490caac2b8cfa5e62d1b28a5e7dba7600e623c71352acbc9b23c2b65b7c | 0x7c97313f349608f59a07c23b18ce523a33219d83 | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x000000000000000000000000c2a0ad4bd62676692f9dca88b750bec98e526c42 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x000000000000000000000000c2a0ad4bd62676692f9dca88b750bec98e526c42 | f | 0 | 0 | t | ||||
| … | … | … | … | … | … | … | … | … | … | … | … | … | … | … | … | … | … | … |
| 0x3072e26fc3266da4f18e7be15647d87d2b41bfb14d783b5499cbc630a2e21a06-0xe77bf88cfd863d7041e395940929c5f04af6f056 | 0xe77bf88cfd863d7041e395940929c5f04af6f056 | 22095180 | 2025-03-21 12:15:35+00 | 0x3072e26fc3266da4f18e7be15647d87d2b41bfb14d783b5499cbc630a2e21a06 | 0xc225d6475cf5fb93506c947db351d67f19f55567 | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x000000000000000000000000ff06901f44fe6b20cead85d511a90b5bb6ce3d56 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x000000000000000000000000ff06901f44fe6b20cead85d511a90b5bb6ce3d56 | f | 0 | 0 | f | ||||
| 0x16d3c3b2255e736ebdf8b286ab0d443069967df9dd22ad9c465081d76eee7761-0xc190d094df65cb8937f2c93f0c3b012f157a4b57 | 0xc190d094df65cb8937f2c93f0c3b012f157a4b57 | 22090548 | 2025-03-20 20:44:59+00 | 0x16d3c3b2255e736ebdf8b286ab0d443069967df9dd22ad9c465081d76eee7761 | 0xc225d6475cf5fb93506c947db351d67f19f55567 | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x000000000000000000000000ff06901f44fe6b20cead85d511a90b5bb6ce3d56 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x000000000000000000000000ff06901f44fe6b20cead85d511a90b5bb6ce3d56 | f | 0 | 0 | f | ||||
| 0xe4043bee2161367b959065abe7ecc9bfe1dd6e4ac7edbdfb5b907949e666d0c8-0x7518f88de6449eb2f4694f00b0123a7993fd4364 | 0x7518f88de6449eb2f4694f00b0123a7993fd4364 | 22090517 | 2025-03-20 20:38:47+00 | 0xe4043bee2161367b959065abe7ecc9bfe1dd6e4ac7edbdfb5b907949e666d0c8 | 0xc225d6475cf5fb93506c947db351d67f19f55567 | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x000000000000000000000000ff06901f44fe6b20cead85d511a90b5bb6ce3d56 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x000000000000000000000000ff06901f44fe6b20cead85d511a90b5bb6ce3d56 | f | 0 | 0 | f | ||||
| 0x6a7f5f44cde0310e0fdc2ba6d0c0a0be7d31521decf9b931abb7370dddb2a1bc-0x0107006da856f5225ee585a2316a0339209f4439 | 0x0107006da856f5225ee585a2316a0339209f4439 | 22082089 | 2025-03-19 16:24:23+00 | 0x6a7f5f44cde0310e0fdc2ba6d0c0a0be7d31521decf9b931abb7370dddb2a1bc | 0xc225d6475cf5fb93506c947db351d67f19f55567 | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x000000000000000000000000ff06901f44fe6b20cead85d511a90b5bb6ce3d56 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x000000000000000000000000ff06901f44fe6b20cead85d511a90b5bb6ce3d56 | f | 0 | 0 | t | ||||
| 0x2eacee1c8171629ae746b5154528abc9c475e20cbef43d0241b7ff8bbbcae7fe-0xff06901f44fe6b20cead85d511a90b5bb6ce3d56 | 0xff06901f44fe6b20cead85d511a90b5bb6ce3d56 | 22061719 | 2025-03-16 20:06:11+00 | 0x2eacee1c8171629ae746b5154528abc9c475e20cbef43d0241b7ff8bbbcae7fe | 0xc225d6475cf5fb93506c947db351d67f19f55567 | 0x000000000000000000000000c225d6475cf5fb93506c947db351d67f19f55567 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x000000000000000000000000c225d6475cf5fb93506c947db351d67f19f55567 | f | 0 | 0 | f | |||||
| 0x75a99e82eeee3b1b16011e675cc77fc57dbf6a329b8cb82b65ded2c6205ce3da-0xbe6e26e881f73d2b1c4973c097cbcb0d96394601 | 0xbe6e26e881f73d2b1c4973c097cbcb0d96394601 | 22061690 | 2025-03-16 20:00:11+00 | 0x75a99e82eeee3b1b16011e675cc77fc57dbf6a329b8cb82b65ded2c6205ce3da | 0xc225d6475cf5fb93506c947db351d67f19f55567 | 0x0000000000000000000000000000000000000000000000000000000000000001 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x0000000000000000000000000000000000000000000000000000000000000001 | f | 0 | 0 | f | |||||
| 0x48be9659f607b16def86754f68f43831f143ceeb013cab46f6bb4d8162dcc063-0xd72d6f0ca177d86230c9bf987912cbf9f6510d2a | 0xd72d6f0ca177d86230c9bf987912cbf9f6510d2a | 22060681 | 2025-03-16 16:36:35+00 | 0x48be9659f607b16def86754f68f43831f143ceeb013cab46f6bb4d8162dcc063 | 0x00bda7096754410b9caa2b559fb263cda1b1b243 | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x000000000000000000000000b6f3c830d289db8d12c5e15b8d558539d0efd83a | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x000000000000000000000000b6f3c830d289db8d12c5e15b8d558539d0efd83a | f | 0 | 0 | t | ||||
| 0xec62e8b1c9f47c73825cab1c680c18cf27c41b66c77433aa5ae178455187336a-0xb5a58db25eedefeede888f55d6157e13d4b4f4f8 | 0xb5a58db25eedefeede888f55d6157e13d4b4f4f8 | 21892111 | 2025-02-21 03:44:59+00 | 0xec62e8b1c9f47c73825cab1c680c18cf27c41b66c77433aa5ae178455187336a | 0x00bda7096754410b9caa2b559fb263cda1b1b243 | 0x0000000000000000000000000000000000000000000000000000000000000000 | 0x000000000000000000000000b6f3c830d289db8d12c5e15b8d558539d0efd83a | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x000000000000000000000000b6f3c830d289db8d12c5e15b8d558539d0efd83a | f | 0 | 0 | f | ||||
| 0x483c9796a09d3c2de8da8d148fb3f609abcd320f077c7ee2a5b440ed09a754d7-0xb6f3c830d289db8d12c5e15b8d558539d0efd83a | 0xb6f3c830d289db8d12c5e15b8d558539d0efd83a | 21864627 | 2025-02-17 07:31:35+00 | 0x483c9796a09d3c2de8da8d148fb3f609abcd320f077c7ee2a5b440ed09a754d7 | 0x00bda7096754410b9caa2b559fb263cda1b1b243 | 0x00000000000000000000000000bda7096754410b9caa2b559fb263cda1b1b243 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x00000000000000000000000000bda7096754410b9caa2b559fb263cda1b1b243 | f | 0 | 0 | f | |||||
| 0x58e6db7577cae38d4eabde3817d0325b099854b3bcb2e0df0d5943feb3b738a2-0x916ff94ad30bdf0559c7f858f7fe3e437fd11a08 | 0x916ff94ad30bdf0559c7f858f7fe3e437fd11a08 | 21864585 | 2025-02-17 07:22:59+00 | 0x58e6db7577cae38d4eabde3817d0325b099854b3bcb2e0df0d5943feb3b738a2 | 0x00bda7096754410b9caa2b559fb263cda1b1b243 | 0x0000000000000000000000000000000000000000000000000000000000000001 | 1 | 100 | DEFINITIVE: CPIMP storage slot STOR_FF36_OPERATOR written with value 0x0000000000000000000000000000000000000000000000000000000000000001 | f | 0 | 0 | f |
Table truncated for readability. Full data available upon request.