Preliminary Postmortem: The CPIMP Attack on USPD Protocol
On December 4th, 2025, the USPD protocol was exploited through a sophisticated attack vector known as CPIMP (Clandestine Proxy In the Middle of Proxy). This document serves as a preliminary postmortem to explain what happened, how it happened, and what steps we are taking in response.
This was not a flaw in our smart contract logic. The USPD protocol underwent rigorous security audits by top-tier firms Nethermind and Resonance. Our code is fully unit-tested and adheres to strict industry standards. Instead, we were targeted by an attack that exploited the deployment process itself.
What is a CPIMP Attack?
CPIMP (Clandestine Proxy In the Middle of Proxy) is a sophisticated attack that hijacks uninitialized upgradeable proxy contracts by inserting a malicious “middleman” contract between the proxy and its legitimate implementation.
The attack is particularly dangerous because it is completely transparent to normal protocol operation—users, developers, and even block explorers like Etherscan see the legitimate implementation, while the attacker maintains hidden control.
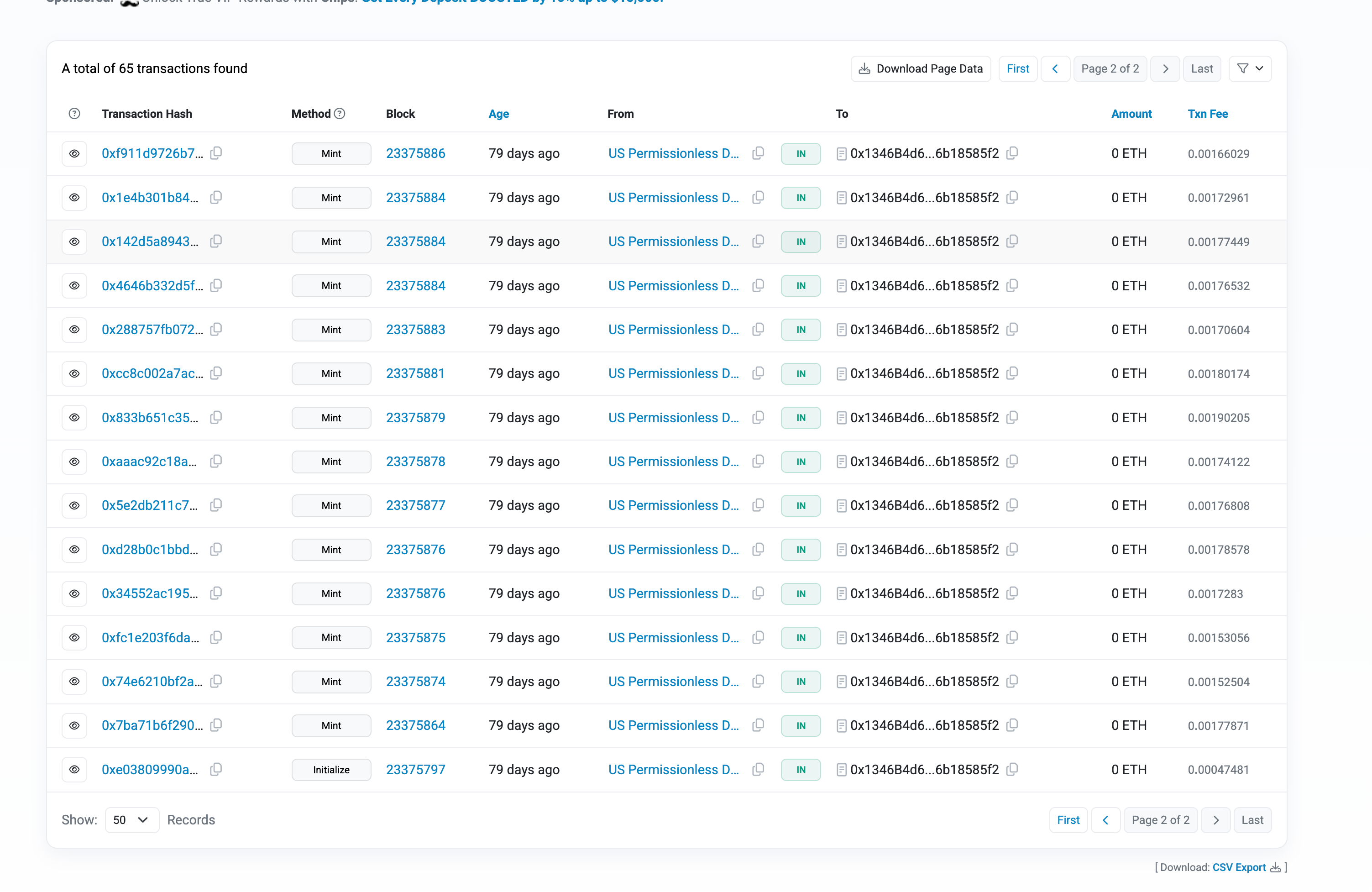
Timeline of Events
| Date | Event |
|---|---|
| Mid-July 2025 | CPIMP attack vector first detected in the wild by security researchers |
| August 20, 2025 | Our final security audit completed. Neither we knew nor the auditing firm informed us about the vulnerability, potentially unaware of this exploit |
| September 16, 2025 | USPD protocol deployed; attacker front-runs initialization and infects our proxy contracts |
| December 4, 2025 | Attacker exploits the infected contracts, draining funds |
Why Detection Was Nearly Impossible
The CPIMP attack that targeted USPD presented unique challenges that made detection extremely difficult:
-
Recent Discovery: The CPIMP vulnerability was only detected in mid-July 2025. By the time we completed our final audit on August 20, 2025, awareness of this attack vector had not yet propagated through the security community.
-
Audit Limitations: We were not aware and our auditors have not informed us about this potential exploit, and it’s likely they were not yet aware of its existence.
-
Modified Attack Variant: The attacker modified their approach from the originally documented CPIMP attack, using different storage slots. This made pattern-matching against known signatures ineffective.
-
Tooling Gaps: External detection tools that could automatically scan for proxy infections with this vulnerability were either:
- Not yet equipped with detection capabilities for this specific attack, or
- Not running/available at the time of our deployment
-
No Warning Signs: We deployed in mid-September completely unaware that this attack vector existed, let alone how to detect it. The attack left no visible traces—our initialization transaction succeeded, Etherscan showed our legitimate implementation, and all protocol functions worked as expected.
In conclusion: At the time of our deployment, detecting this attack was extremely difficult, if not impossible, for any team without specific prior knowledge of the CPIMP vulnerability and its variants.
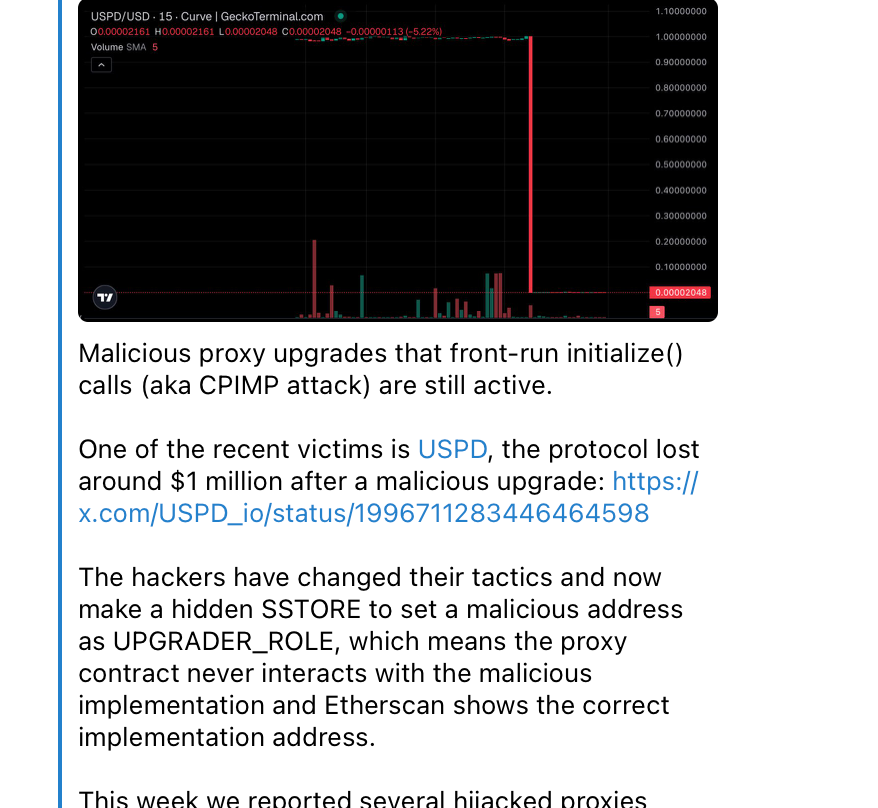
How the Attack Works
1. Target Identification
The attacker monitors the mempool for proxy deployment transactions that haven’t yet been initialized. Upgradeable proxy contracts typically require a two-step process: deployment followed by initialization. This window of vulnerability is what the attacker exploits.
2. Front-running the Initialization
The attacker front-runs the legitimate initialization transaction by calling the proxy’s initializer first, setting themselves as the implementation. In our case, this occurred on September 16th, 2025, via a Multicall3 transaction.
- Infection Transaction: 0xc0b7e490caac2b8cfa5e62d1b28a5e7dba7600e623c71352acbc9b23c2b65b7c
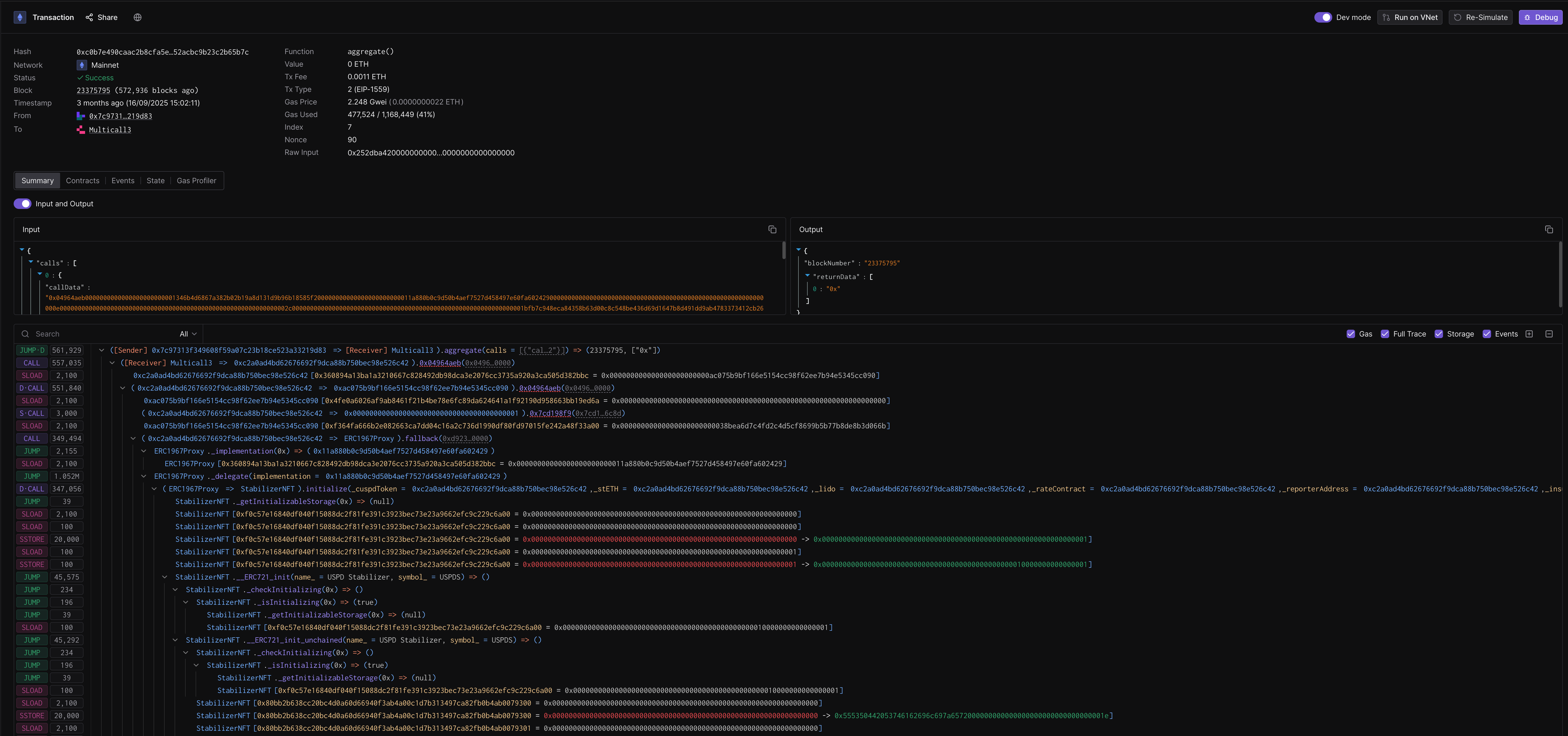
3. Transparent Hijacking
The CPIMP contract operates as an invisible middleman:
- Stores the legitimate implementation address in a custom storage slot
- Sets itself as the proxy’s implementation in the standard ERC1967 slot
- Forwards all calls to the legitimate implementation via a second
delegatecall - The legitimate owner’s initialization transaction succeeds—it doesn’t revert, giving no indication that anything is wrong
This creates a call chain of Proxy → CPIMP → Implementation instead of the expected Proxy → Implementation.
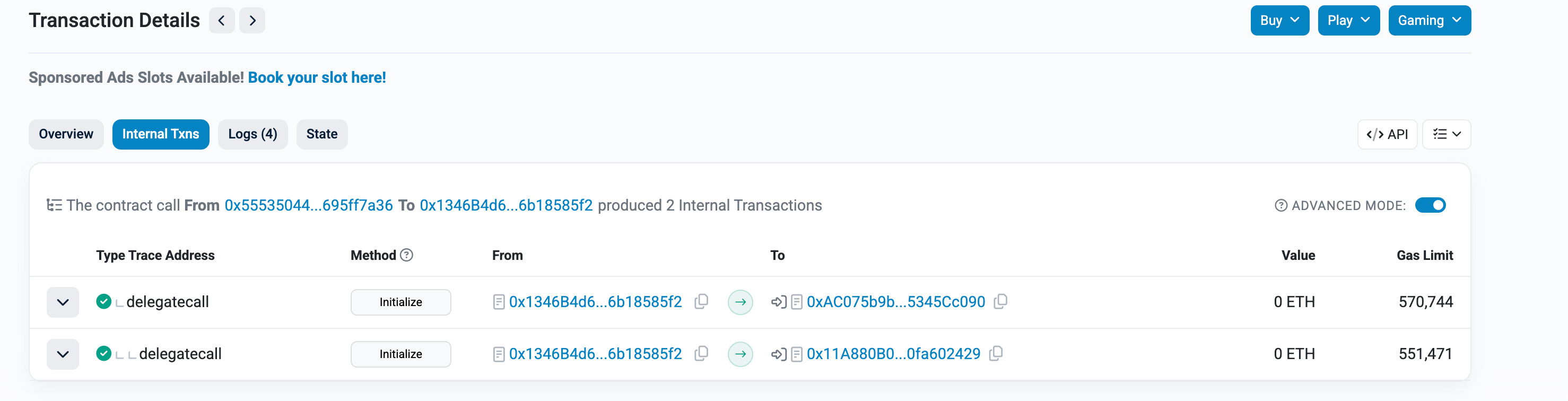
4. Persistence Mechanism
After every transaction, the CPIMP contract restores itself in the implementation slot. This makes it impossible to remove via normal upgrade procedures—any attempt to upgrade the contract simply gets intercepted and neutralized.
5. Admin Hijacking
The CPIMP copies the original admin to a shadow storage slot and replaces it with the attacker’s address. This gives the attacker full administrative control while the original admin appears to retain their role.
- Attacker Address: 0x083379BDAC3E138cb0C7210e0282fbC466A3215A
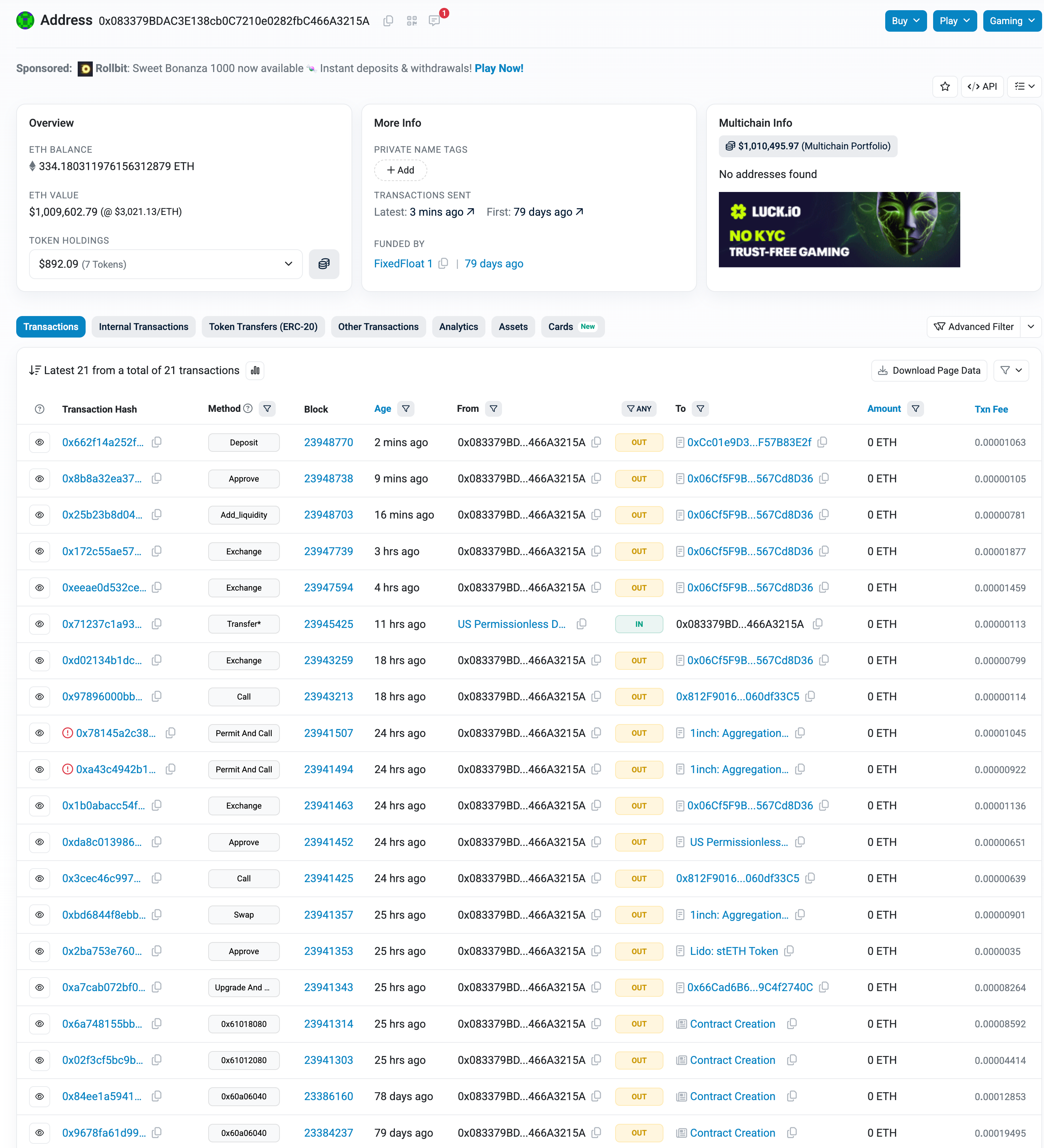
Why This Attack is So Dangerous
| Characteristic | Impact |
|---|---|
| Completely transparent | Normal protocol operation continues unaffected |
| Etherscan spoofing | Block explorers show the legitimate, audited implementation |
| Delayed exploitation | Attacker can wait months before draining funds |
| Upgrade-resistant | Cannot be removed by standard upgrade mechanisms |
| Audit-proof | The deployed code passes all audits because it IS the audited code |
The attacker exploited our protocol on December 4th, 2025—nearly three months after the initial infection.
- Exploit Transaction: 0xa7cab072bf0453301a0ab1b06c49a9405d115824fc617fb42cba9b70f3b893c2
Key Detection Signatures
For other protocols and security researchers, here are the telltale signs of a CPIMP attack:
- Double delegatecall pattern in transaction traces
- Multiple
Upgradedevents emitted in a single transaction - Custom storage slots being written (e.g.,
stor5F36,storFF36,storC3F3if decompiled) - Implementation slot initialized from zero combined with other suspicious activity
- Discrepancy between traced execution and expected implementation
Our Response
Immediate Actions
- ✅ Identified and confirmed the attack vector
- ✅ Immediate and transparent disclosure on all social media channels
- ✅ Direct communication with all partners and investors
- ✅ Flagged attacker addresses at all major centralized exchanges
- ✅ Flagged attacker addresses at major DEXs and DeFi protocols
- ✅ Flagged attacker addresses at block explorers (Etherscan, etc.)
Law Enforcement & Investigation
- ✅ Filed police reports with specialized cybercrime units
- ✅ Filed report with the FBI
- ✅ Engaged law enforcement agencies across multiple jurisdictions
- ✅ Partnered with reputable whitehat security researchers
- ✅ Actively working to identify and unmask the person or group behind the attack
Community & Partner Support
We are grateful for the continued support from our partners and investors during this challenging time. Their immediate response and assistance has been invaluable in our recovery efforts.
Ongoing Investigation
We are conducting a thorough forensic analysis of the attack and will publish a complete postmortem once our investigation concludes.
Whitehat Offer
To the attacker: We have already reached out via on-chain message requesting the return of funds. We remain open to treating this as a whitehat rescue.
If you return the funds (minus a 10% bug bounty), we will:
- Cease all law enforcement actions
- Publicly acknowledge this as a whitehat hack
- Provide a formal letter of non-pursuit
A word of caution: We are working with traditional law enforcement and special crimes units across multiple jurisdictions, monitoring every touchpoint where a standard IP address (or locale, etc) would interact with a server such as a DEX for a swap or an on-ramp of off-ramp service. Six months is a long time. If at any point during that period (even once) a VPN was forgotten, a window left open, or a wallet connected without proper operational security, we will find out. The digital trail is being meticulously reconstructed.
The whitehat offer is the path of least resistance. We strongly encourage you to take it.
Contact us at any channel you find appropriate (including a signature from your wallet).
Further Reading
- Dedaub: The CPIMP Attack—An Insanely Far-Reaching Vulnerability Successfully Mitigated
- Security Researcher Analysis on X
What’s Next
The Path Forward
We will continue to be transparent. This situation, while challenging, will not be the end of USPD.
Here’s what we believe:
- Our protocol was diligently audited by Nethermind and Resonance. The smart contract logic is sound.
- Our contracts were not the culprit. This was an attack on the deployment process, not on our code.
- There is a need for a fully decentralized, transparent Dollar
We are actively working on a recovery plan to make affected users whole. While we cannot promise specifics yet, we are exploring options that would allow participants to benefit from future protocol revenue and growth. The details are still being finalized, but our goal is to present an offer that acknowledges the losses while providing a genuine path to recovery.
A Call to Our Community
Any project lives or dies with its community. And our community has proven to be relentlessly committed to DeFi without TradFi ties. That commitment is what will carry us through this.
We need your help:
If you have connections to specialized cybercrime units or reputable whitehat hackers in China or Singapore, please reach out to us immediately. Any lead that helps identify or recover funds will be invaluable.
Continued Updates
We will continue to update the community as our investigation progresses. A full postmortem with detailed technical analysis, timeline of events, and remediation plan will be published in the coming weeks.
For real-time updates, follow us on Telegram or Discord .
To our community: We understand the gravity of this situation and are committed to full transparency throughout this process. Thank you for your patience, your support, and your belief in what we’re building together.